|
Fortego Security offers an advanced and flexible service for log analysis. We help you discover hackers, trojans, worms and other immediate threats, while at the same time providing continuous high quality material on which you can base general risk management decisions. A good overview of what is really going on in a network or server room is fundamental to good planning, which in turn is crucial to good design and security.
We offer this service for anything from single servers and small LANs, to extensive server parks and global VPN solutions. The depth and extent (and thus price) of the service can also be easily adapted to your exact needs, anything from a couple of hours of simple analysis per month, up to any level of complexity and resources that you find yourself in need of.
So, what then might the benefit and purpose of a log analysis service be? Logs and log analysis is commonly extremely underrated both in terms of increased overall security, stability and availability. The money spent on even the most simple types of analyses are generally quickly regained in form of the valuable information, security and overview that results.
Most companies constantly produce logs from hundreds, if not thousands, of systems. But if these logs are not reviewed to extract the valuable information they contain, what is then their purpose at all, except possibly to provide a false sense of security?
To further illustrate the value of our log analysis service, let us mention a few categories of information and effect that our analyses have generated in actual cases:
- During the course of our collected log analyses, we have discovered trojans, viruses and other similar hacker tools that not even the antivirus companies have known about or recognized. This means that these malicious programs have been able to, completely undisturbed in any way, penetrate into and infect/attack computers with access to extremely sensitive information inside large companies and institutions. The malicious code has in these cases been immediately removed upon our alert, and potential catastrophes have been possible to avert.
- Similar to the cases with previously unknown trojans, viruses and hacker tools, we have also during our analyses discovered several previously unknown vulnerabilities in commercial software products, that hackers have been using to attack public servers of the customers in question. Such servers are often considered relatively safe as long as they have all the latest patches, but that's hardly of any help when the exploited vulnerabilities aren't publicly known yet, now is it? In these cases countermeasures have been immediately taken by the customers, in order to maintain integrity of the servers.
- Also in cases of seemingly unexplainable worm and virus outbreaks inside closed LANs, these have been possible to immediately trace to the source (e.g. a laptop connected to the LAN by a consultant), and the threat has been possible to neutralize with minimal resources.
- Configuration problems related to both network infrastructure (like routers and firewalls) and other networked systems (like e.g. email or DNS servers) used by the customer in question are often detected and corrected during our running analyses. Many of these problems would have been very hard to detect using other methods, and would thus have remained for long periods of time, possibly years, causing problems for the daily operations.
Many organizations never take (or even have) the time to analyze the overwhelming volume of logs being generated by its web servers, firewalls, IDS nodes and similar systems. With our knowledge, experience and custom developed log analysis system, we extract invaluable information out of your gigabytes of logged raw data, which is then presented in neat and easily read reports.
When something suspicious is detected in a log file, it is often a great loss to content oneself with this limited observation, and the even more limited information implied by it. Rather, what is most desirable in this situation is an efficient way to extract as much information as possible about any other activity that is in any way related to the same event, attack or attacker(s), irrespective of the size or complexity of the incident. Our analysis system is designed from the bottom up with this type of advanced data correlation in mind, and our knowledge and experience from hundreds of actual scenarios form the foundation of its well-devised design.
How would you go about identifying the source computer of trojan traffic in an environment using dynamic IP addresses? Or what about if the computer is sometimes locally connected to a LAN, and sometimes connected through a VPN based distance workplace? To handle this kind of situations, our service includes a type of session aware analysis where the real computers are identified by correlation of e.g. DHCP, VPN and firewall logs, easily adaptable to handle the types of sessions and logs occurring in your specific network environment.
When it comes to prioritizing and classifying detected attacks, we also take into account the software actually running on the different systems in question. For example, a worm designed to attack Microsoft IIS web servers would very seldomly cause any harm whatsoever to a Lotus Domino web server, which would in that case be taken into account. Based on our vast experience of different kinds of penetration testing, we have a deep understanding of how attacks against e.g. Windows and Unix systems differ technically, which we have also used to maximize the efficiency of our log analysis system.
Which logs then can be used for this service of ours? The truth is that our system is designed to be quickly adaptable to practically any type of logs you might want to analyze. This extendability and flexibility means that whether it concerns a common Apache web server or a complex customized system that noone else than you have access to, the powerful engine of the analysis system can be used to analyze these logs after a minimal initial adaption procedure at its most, which we will of course perform for no charge whatsoever.
A few commonly analyzed log types worthy of mention are e.g. firewall logs, IDS logs, IPS logs, integrity/tampering checking logs (e.g. from Tripwire), web logs, VPN logs, DHCP logs, DNS logs, operating system logs, antivirus logs, database transaction logs, email logs, FTP logs, and application logs of assorted types.
For better overview, these can be separated into the four common log categories communication logs (firewall, VPN, web, FTP, email, ...), operating system logs, protection application logs (IDS, IPS, antivirus, integrity/tampering, ...) and business application logs (databases, economy systems, ...).
For the logs in the protection application category (see above) we can also assist you with continuous recommendations regarding suitable updates and modifications of rules and policy files, in order to e.g. make your IDS or integrity/tampering checking system even more efficient.
Contrary to what product companies of all kinds would ever willingly admit, we are well aware that a computer system left completely on its own could never perform these kinds of tasks to any satisfying or value generating degree. That is why we have experienced and knowledgeable operators controlling and utilizing the advanced analysis system from start to end, forming the analysis process based on the unique conditions and events in your specific case. Also the reports that are regularly delivered to our customers are created by human operators.
Depending on your specific situation, we can offer the service in the form of anything from actual visits to your offices, to direct transfer of log data to our lab over secure connections. We also offer to archive your logs (securely encrypted of course). This provides an extra layer of protection in case an accident, intrusion or other type of incident would result in the corruption or even complete loss of your log copies. We can also offer prepared log servers for use in local data collection.
If you have any inquiries or want more information of any kind, please contact us by e-mail at
|
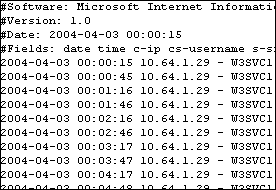
Web server logs can often be overwhelming for the human eye. But with
our advanced custom built system, logs are analyzed efficiently.
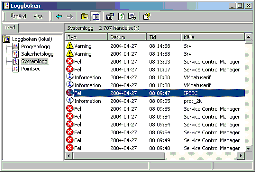
Windows EventLog messages can often be hard to understand, even for IT administrators.
|